Introduction to the Test
DDoS Training Service Guide
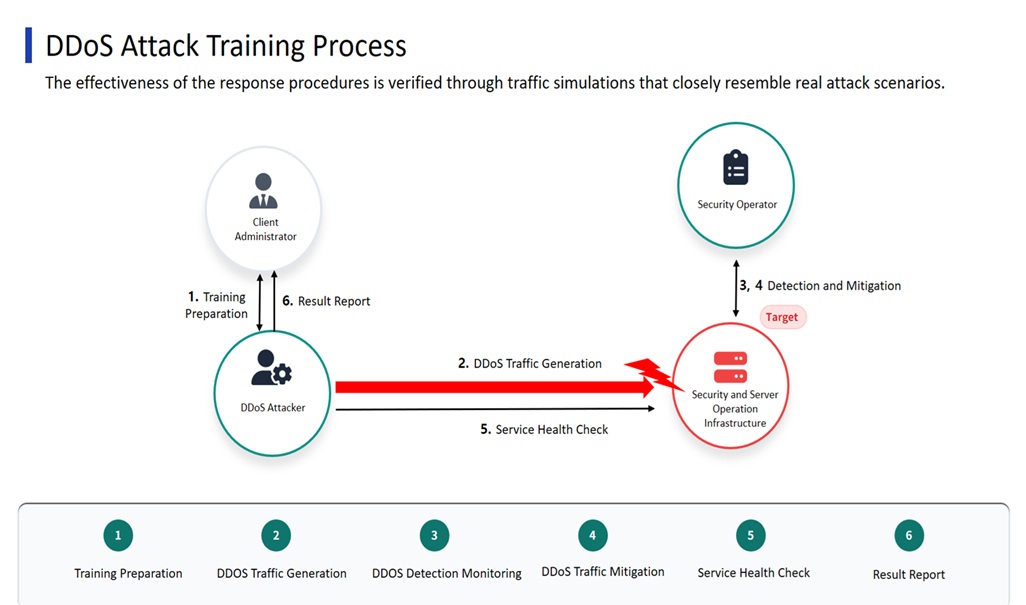
This is a real-world training service to evaluate whether your organization's detection and response procedures against large-scale traffic-based service disruption attacks (DDoS) are actually functional.
By applying customized scenarios based on actual attack types, we verify whether detection time, decision-making speed, and equipment/policy response are appropriately carried out during a sudden increase in traffic.
"5,800 domestic security incident reports over 3 years, with a surge in DDoS attacks!"
DDoS doesn't just stop the service. It halts the entire business operation, and business disruption leads to personnel incidents. An untrained organization cannot respond effectively in a real attack.
WHY? The Need for Training
- The core cause of recent service disruption incidents is often inadequate response procedures and failure of initial judgment.
- A DDoS attack will lead to a complete service outage if not mitigated within 5 to 10 minutes after detection.
- 1 hour of downtime -> Revenue loss - customer complaints - damaged reputation.
- DDoS cannot be prevented by technical defense alone; the immediate response of the operations team is vital.
- Over 70% of actual incidents are escalated due to the absence of operational procedures and delayed decision-making.
Industry sector
Test Standard
Tisk The Fatal Risks Created by Lack of Traing
1. Risk of personnel incidents and operational failures.
2. Immediate damage to revenue and credibility due to service disruption.
3. Sharp decline in operational efficiency and work accuracy due to work delays.
4. Severe damage to reputation and brand value due to increased customer complaints.
5. Explosion of organization-wide service outage and recovery time if the response is delayed.
6. Targeting for re-attack as an organization with weak defenses.
-
Contact Person
- Cybersecurity
-
greenjs@icrqra.com

